
Why is Zero-Trust Wi-Fi (ZTW) framework critical to addressing Enterprise Security gap?
This article delves into the essential role of Zero Trust Wi-Fi (ZTW) in bridging the last-mile Enterprise security gap.
With the rapid evolution of sophisticated cyber threats, traditional security measures like perimeter-based firewalls, though important, are no longer sufficient, necessitating a shift to more dynamic and robust Cloud-Security architecture.
The Shifting Network Security Landscape
The shift from physical network perimeters to Software-Defined Networks (SDNs) is rapidly changing our understanding of network security, especially when it comes to complex network architectures. The surge in remote work, the expansion of Wi-Fi infrastructures, and the proliferation of connected devices, IIOT (Industrial internet of things) OT (Operational Technologies), and IoTs (Internet of Things - connected objects) render traditional security approaches obsolete.
Zero Trust Network Access (ZTNA): A New Security Paradigm
Enter Zero Trust Network Access (ZTNA). Moving away from the dated "fortress" model of security, ZTNA operates on a foundational principle of never assuming trust – even within an organization's network. This approach requires rigorous verification for every entity (users and devices) seeking access, drastically changing the security landscape.
The Crucial Role of Identity in Zero Trust
Transitioning from securing physical perimeters to securing digital entities (users and devices) underscores the importance of a robust Identification and Authentication Framework. Zero Trust mandates that identity and authentication should be central to any organization's cybersecurity strategy. This includes ensuring the security of user, device, and IoT endpoint identities across both wired and wireless networks.
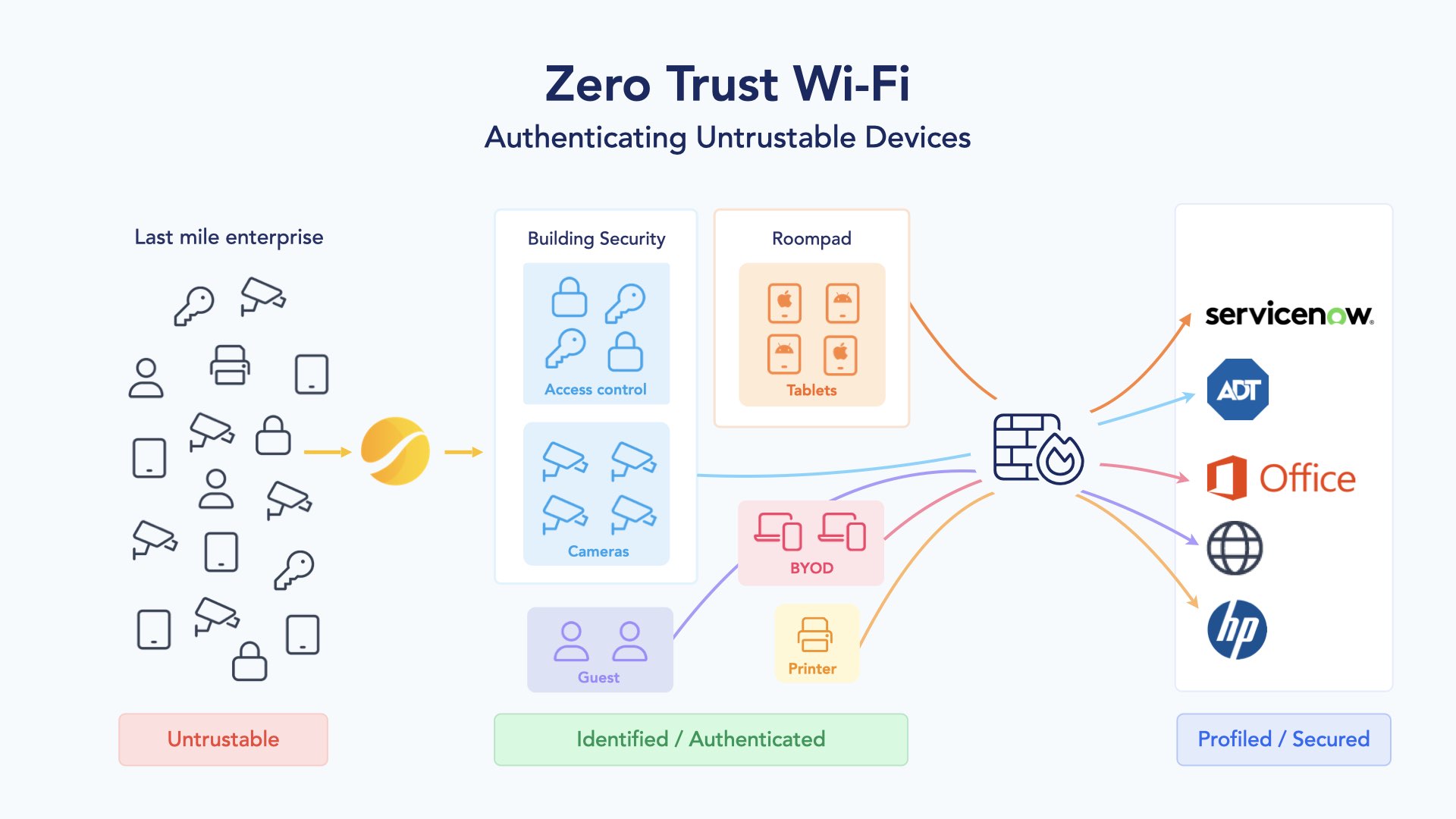
So what is Zero Trust Wi-Fi (ZTW)?
Zero Trust Wi-Fi (ZTW) is an advanced security architecture that fundamentally shifts the approach to cybersecurity in Wi-Fi network environments.
Unlike traditional security models that operate on the assumption that everything inside an organization's network can be trusted, the Zero Trust model operates under the principle of "never trust, always verify." This means that every device, even if it is an IT asset of the organization, is treated as potentially untrustworthy and must be authenticated and authorized before being granted access to any network resource.
In the context of Wi-Fi networks, Zero Trust architecture plays a crucial role in enhancing security. Wi-Fi networks, due to their broadcast nature and the sensitivity of the data they often carry, are particularly vulnerable to attacks. By integrating Zero Trust principles into Wi-Fi security strategies, organizations can ensure that only authorized users and devices are granted access to the network. This approach helps to mitigate risks such as unauthorized access and lateral movement within the network, thereby significantly reducing the exposure of sensitive data.
Key aspects of Zero Trust Wi-Fi (ZTW) architecture include:
- Explicit Verification: Every access request is evaluated based on multiple factors like user identity, device health, and network context. This ensures that trust is not automatically granted, even to previously authenticated users or devices.
- Least Privilege Access: Limiting the amount of information and the duration for which people can access network resources rather than allowing indefinite access to all company resources.
- Assume Breach: Segmenting networks to contain damage in the event of a breach and requiring end-to-end encryption.
Navigating Zero Trust WiFi (ZTW) to Close Internet Security Gaps
The consensus today is clear: Zero Trust must begin with Identity. This means authenticating and identifying every user and every device (including IIOT, OT and IoT) before granting Internet access.
Zero Trust Cloud Security: The Next Frontier
Zero Trust cloud security is integral to this paradigm. It extends the principles of Zero Trust to cloud environments, ensuring that data and resources in the cloud are as secure as those on-premises. This is particularly important as more organizations migrate to cloud-based services, requiring robust security measures to protect sensitive data.
Incorporating Cloud Solutions into Zero Trust WiFi (ZTW)
Cloud Captive Portal solutions and Cloud-based Dynamic Host Configuration Protocol (DHCP) solutions play a vital role in managing Wi-Fi network security within a Zero Trust framework. They provide streamlined, secure onboarding and enhance overall network security, making them indispensable tools in the Zero Trust arsenal.
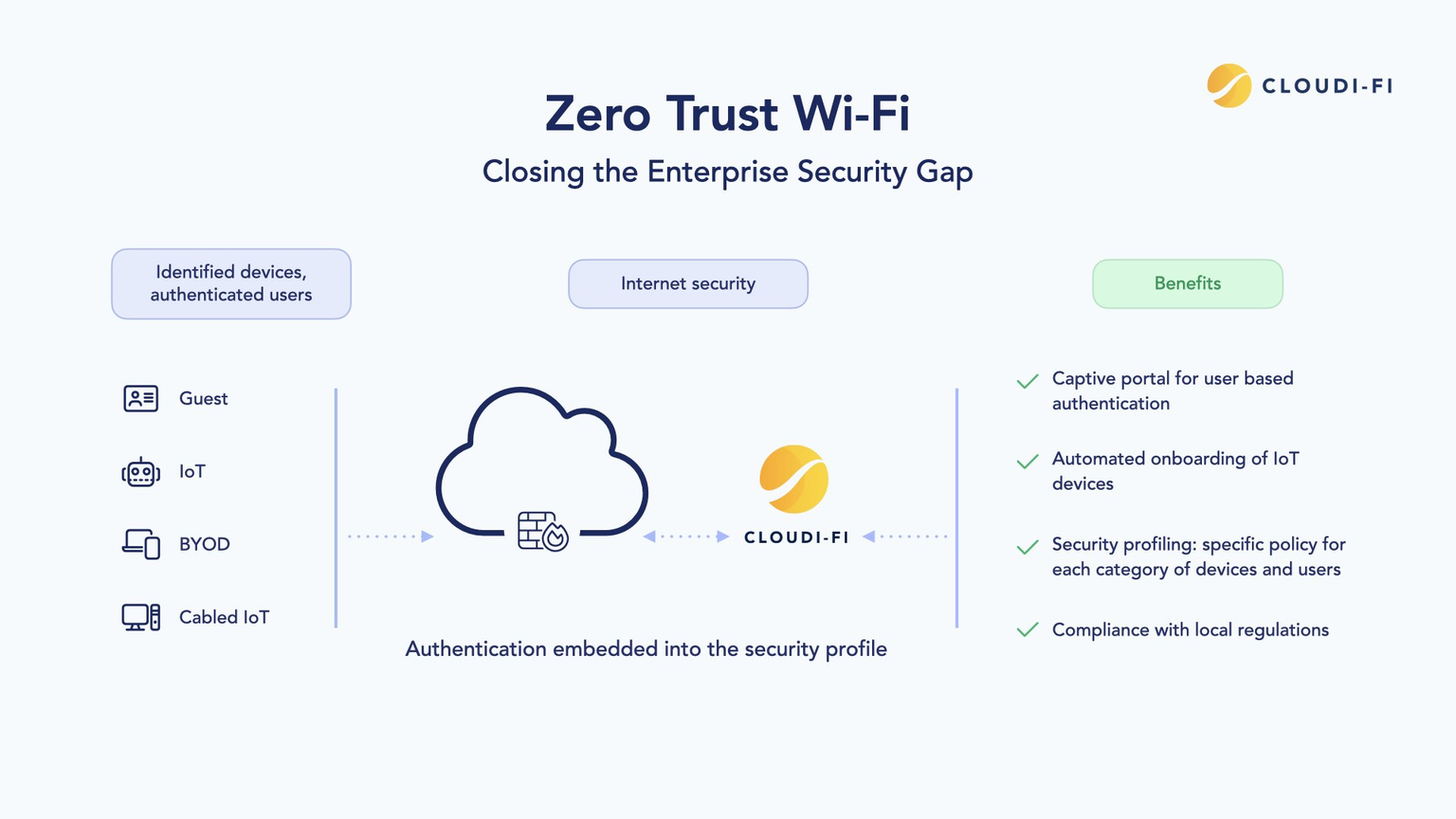
The Emergence of Zero Trust Wi-Fi (ZTW)
The advent of Zero Trust Wi-Fi signals a new era of trust and security in wireless environments. This revolutionary approach dictates that trust is earned and continuously verified, even within your Wi-Fi network.
Architecting a Secure Digital Future
Zero Trust is not just a security philosophy; it's a necessity in our evolving digital landscape.
Zero Trust Wi-Fi and Zero Trust cloud security extend beyond traditional network boundaries, offering a comprehensive approach to cybersecurity.
Implementing Zero Trust Wi-Fi architecture involves steps like strong identity verification, managing access to devices and networks, and ensuring compliance with security requirements. Techniques like AP Isolation, individualized VLANs for users or devices, individual VPNs, and multi-factor authentication (MFA) are often employed to enforce Zero Trust principles in Wi-Fi networks.
The benefits of using Zero Trust Wi-Fi security principles will improve the overall security while supporting remote and hybrid work models, and facilitating the migration to cloud environments while improving guest and employee user experience with simplified access to resources.
In this context, Cloud Captive Portal solutions facilitate secure onboarding, while Cloud-based DHCP solutions enhance the management of IIot, OT and IoT networks, delivers automated untrusted device fingerprinting and profiling, all within Zero Trust framework principles.
Zero Trust Wi-Fi stands as the bedrock of modern cybersecurity, fortifying wireless networks and ensuring that every device adheres to stringent security protocols. This approach is imperative for organizations looking to protect their assets in an increasingly interconnected and vulnerable digital world.
Learn more about Cloud-based DHCP solutions in our latest knowledge base article.
Learn more about Zero Trust Wi-Fi Success Stories

